Why end-to-end encryption is crucial for developer secrets management
- Blog
- Why end-to-end encryption is crucial for developer secrets management
End-to-end encryption for secrets management contributes directly to the overall security of a business. Developers must ensure that their data is safe and secure, and end-to-end encryption is a powerful way to do this. Let’s explore different encryption methods and why end-to-end encryption is the right choice for development teams who are evaluating secrets management solutions.
End-to-end encryption is a cryptographic method that prevents unauthorized parties from accessing a string of data while it is transmitted. This data is encrypted at one endpoint and decrypted at another endpoint, ensuring only the sender and receiver can decrypt and read the data — provided they have the encryption key.
Utilized globally by organizations, end-to-end encryption secures the world’s most sensitive data. Vendors that manage high volumes of user data and fail to implement the highest security measures such as end-to-end encryption have come under scrutiny. Google, for example, came under fire by both security researchers and users for not including it in their Google Authenticator product. In response, Google announced that they will be bringing end-to-end encryption to “a future version of Google Authenticator.”
End-to-end encryption is crucial for any development team who would like to securely manage their secrets like API keys, database passwords, and SSL/TLS certificates. If these secrets — and the confidential information they protect — were to be exposed to the public, there would be disastrous consequences for the business and its customers.
Many notable companies have experienced the effects of large-scale data breaches that could have been prevented by end-to-end encrypted secrets management. For example, Binance, a cryptocurrency exchange company, suffered a data breach in 2022 that leaked the account information of 1 billion customers including names, mailing addresses, phone numbers, and medical records. Attackers were able to access such confidential customer information via a plain text access credential listed in a code snippet.
Securing developer secrets with end-to-end encryption in a centralized location — like a dedicated secrets manager — can better protect sensitive information from unauthorized access and reduces the possibility of a data breach.
Other encryption methods are not secure enough to protect your critical secrets
Not all encryption methods are made equal. Unfortunately, many secrets management solutions on the market utilize cryptographic methods that are less secure than end-to-end encryption, jeopardizing the safety of your privileged developer secrets. Let’s dive a little deeper into the differences between popular encryption methods used in secrets management solutions.
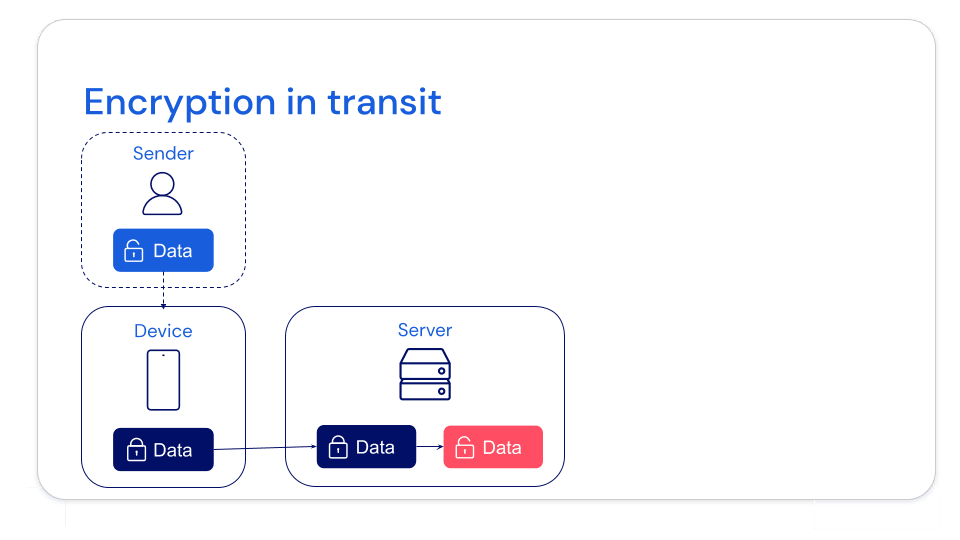
Encryption in transit
Many secrets managers utilize encryption in transit to protect your secrets, which is less secure than end-to-end encryption. With encryption in transit, data is only encrypted when it is active and moving between devices, networks, or infrastructures.
In the example below, the data is only encrypted when it moves from the sender’s device to the server — leaving the server-side data unprotected from potential attacks.
Encryption at rest
Other secret management solutions also use encryption at rest to secure secrets. This method encrypts data when it is not actively being used and stored in a location like a hard drive, laptop, flash drive, or cloud storage. The combination of encryption at rest and encryption in transit provides slightly stronger security, but there are still gaps in its protection.
In the example below, the data is decrypted before it is moved to the storage container — leaving a potential access point for malicious actors.

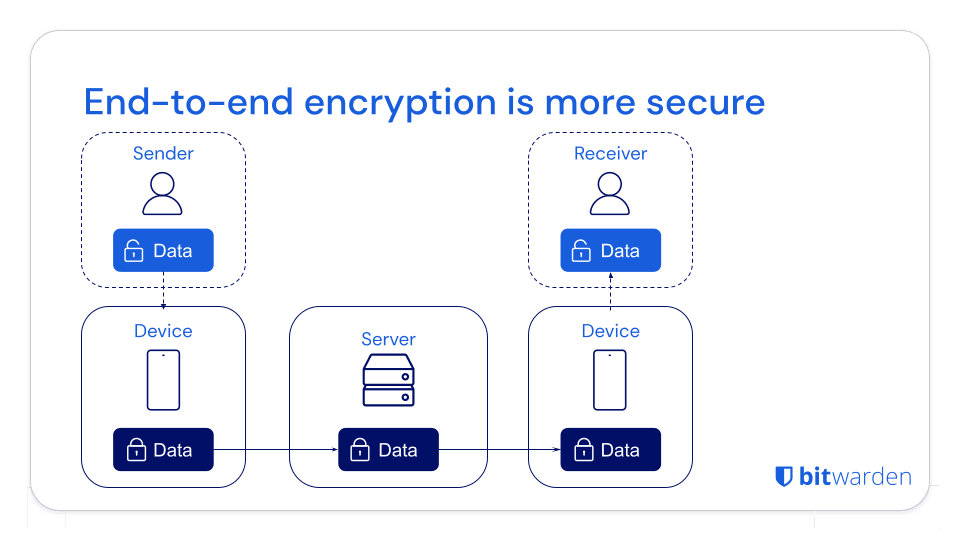
Bitwarden secures your critical secrets with end-to-end encryption
End-to-end encryption is more secure than other encryption methods. With end-to-end encryption, the data is immediately encrypted and NEVER decrypted as it passes from the sender to the recipient, ensuring complete security as the information is transmitted and significantly reducing the possibility of a data breach.
Bitwarden Secrets Manager is a zero knowledge, end-to-end encrypted, and open source solution for securely storing, managing, automating, and sharing secrets at scale across the development lifecycle. With zero-knowledge, the encryption key is not accessible by the service provider, further ensuring the security of your end-to-end encrypted data. Because Secrets Manager offers one centralized location for managing secrets it reduces the sprawl of secrets across the organization and enables administrators to monitor and manage access to sensitive information and systems.
Bitwarden Secrets Manager security posture is stronger than other secrets management solutions on the market. In addition to zero knowledge, end-to-end encryption, Bitwarden Secrets Manager benefits from annual third-party security audits that include source code assessments and penetration testing across Bitwarden IPs, servers, and web applications. The active Bitwarden community also conducts informal source code audits on GitHub and via the Hacker One public bug bounty program.
Bitwarden uses multiple layers of encryption to secure your data — AES-CBC 256-bit encryption for your vault data, and PBKDF2 SHA-256 or Argon2 to derive your encryption key. Data can only be decrypted with the encryption key derived from your master password.
Bitwarden is trusted by millions of individuals and businesses across the globe to secure sensitive information and credentials. Get started securing your developer secrets with end-to-end encryption and enable Secrets Manager! Sign up for free or opt for a 7-day business trial to explore all the enterprise features Bitwarden Secrets Manager has to offer. You can also contact sales for a personalized consultation.
To see Secrets Manager in action, join the bi-weekly live demo and Q&A. Register here.