Microsoft Entra ID SCIM Integration
System for cross-domain identity management (SCIM) can be used to automatically provision and de-provision members and groups in your Bitwarden organization.
note
SCIM Integrations are available for Teams and Enterprise organizations. Customers not using a SCIM-compatible identity provider may consider using Directory Connector as an alternative means of provisioning.
This article will help you configure a SCIM integration with Azure. Configuration involves working simultaneously with the Bitwarden web vault and Azure Portal. As you proceed, we recommend having both readily available and completing steps in the order they are documented.
note
Are you self-hosting Bitwarden? If so, complete these steps to enable SCIM for your server before proceeding.
To start your SCIM integration, open the Admin Console and navigate to Settings → SCIM provisioning:
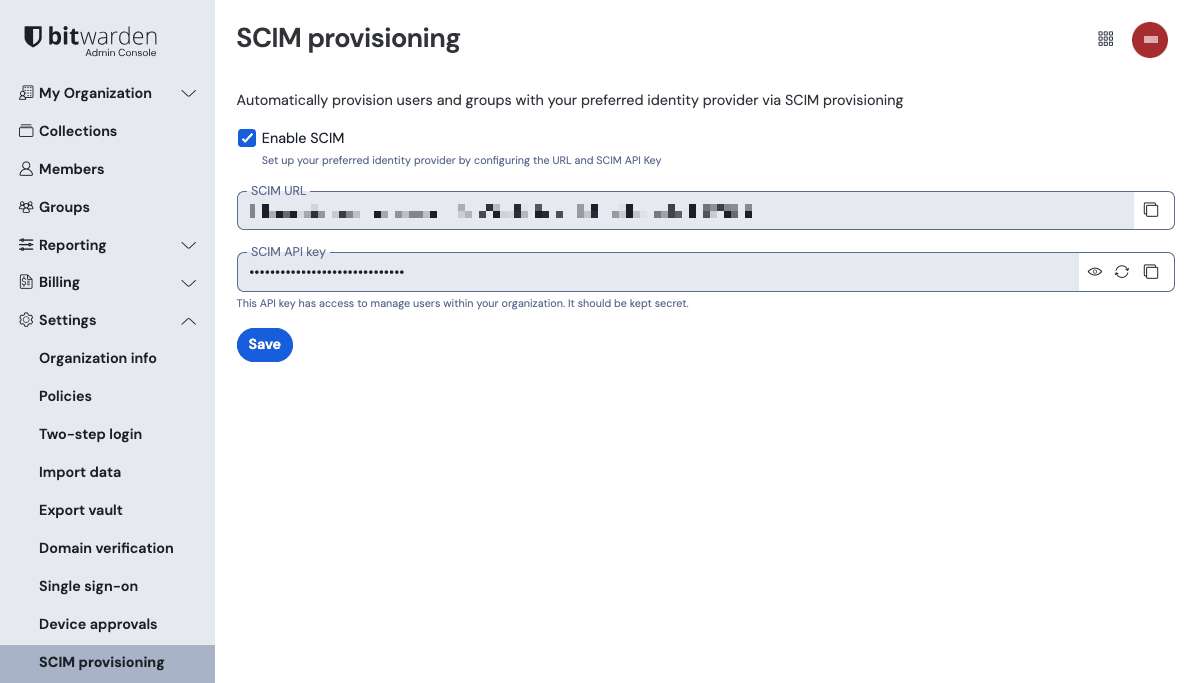
Select the Enable SCIM checkbox and take note of your SCIM URL and SCIM API Key. You will need to use both values in a later step.
tip
If you are already using this IdP for Login with SSO, open that existing enterprise application and skip to this step. Otherwise, proceed with this section to create a new application
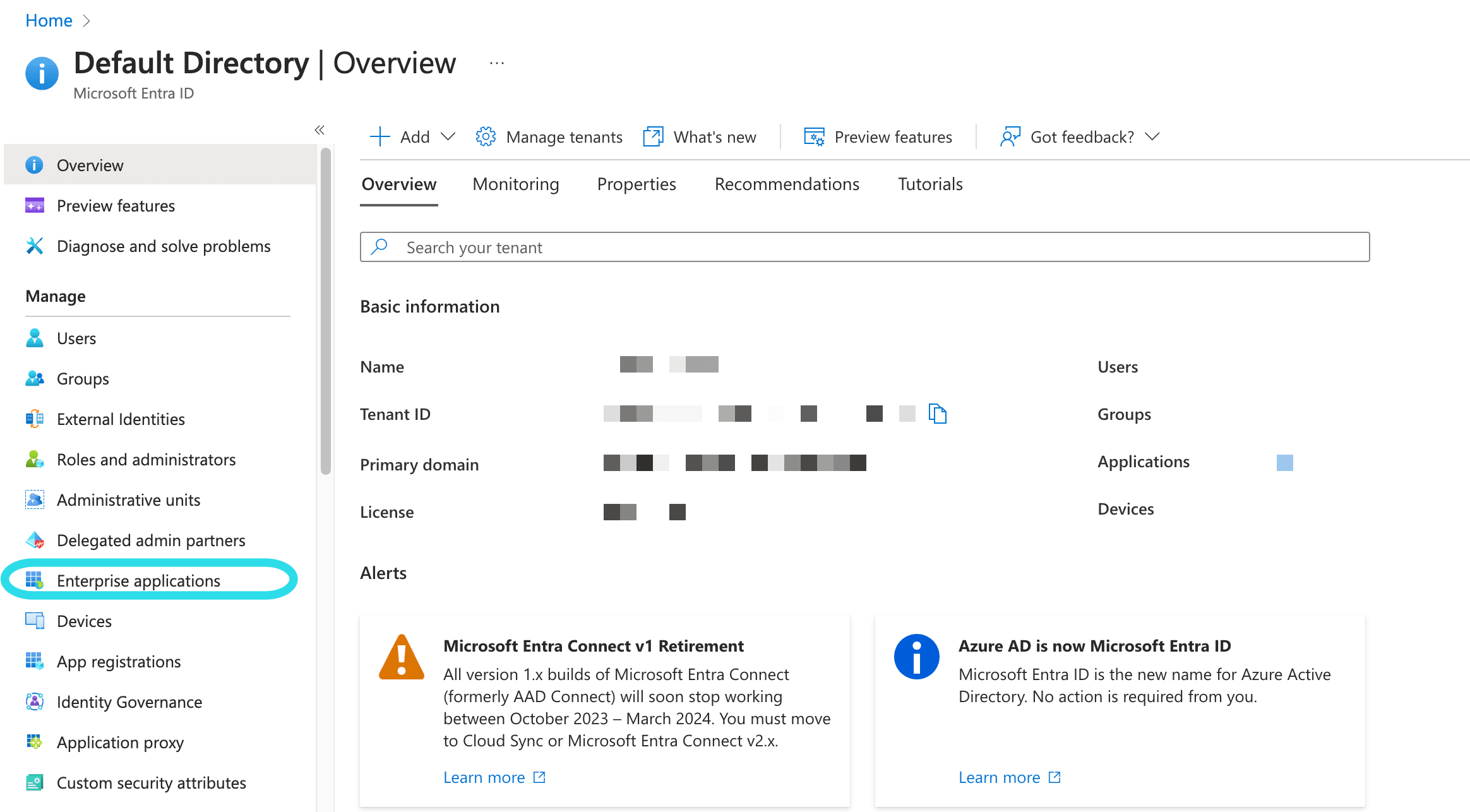
In the Azure Portal, navigate to Microsoft Entra ID and select Enterprise applications from the navigation menu:
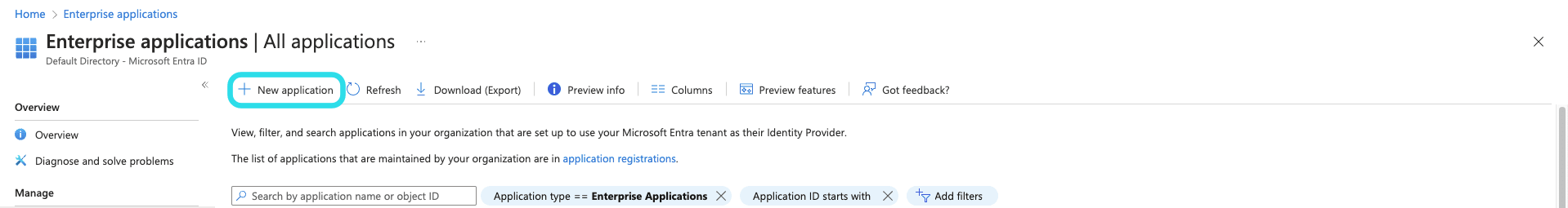
Select the New application button:
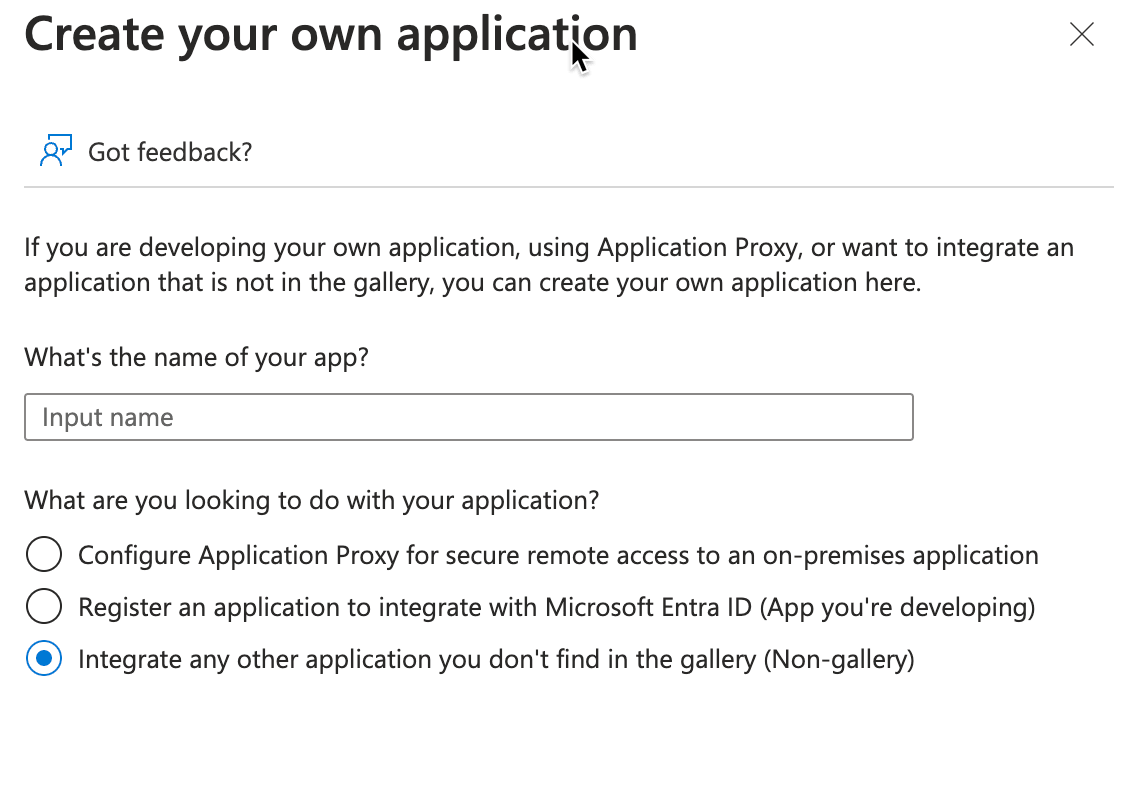
On the Browse Microsoft Entra ID Gallery screen, select the Create your own application button:

On the Create your own application screen, give the application a unique, Bitwarden-specific name. Choose the Non-gallery option and then select the Create button.
Select Provisioning from the navigation and complete the following steps:
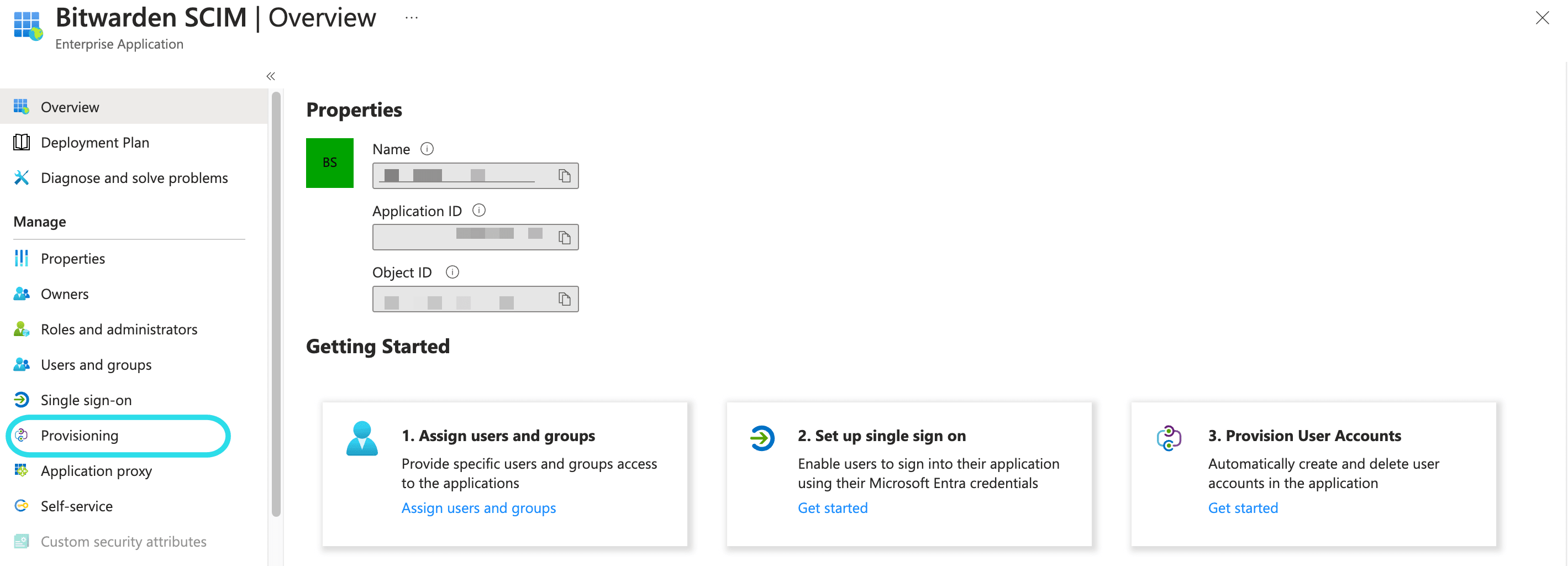
Select the Get started button.
Select Automatic from the Provisioning Mode dropdown menu.
Enter your SCIM URL (learn more) in the Tenant URL field.
Enter your SCIM API Key (learn more) in the Secret Token field.
Select the Test Connection button.
If your connection test successfully, select the Save button.
This screen is available while performing initial setup for the Enterprise Application, or by navigating to the Enterprise Application, and selecting Provisioning under the Manage section of the left-hand menu, and then selecting Edit Provisioning at the top.
Bitwarden uses standard SCIM v2 attribute names, though these may differ from Microsoft Entra ID attribute names. The default mappings will work, but you can use this section to make changes if you wish.
User mapping
If you would like User objects in your directory to synchronize with Bitwarden, you may enable or disable Provision Microsoft Entra ID Users. This is enabled by default. Select the Provision Microsoft Entra ID Users link to customize the attributes sent to Bitwarden with the user objects if you wish to make changes according to the following table:
Bitwarden attribute | Default AAD attribute |
|---|---|
|
|
|
|
|
|
|
|
ª - Because SCIM allows users to have multiple email addresses expressed as an array of objects, Bitwarden will use the value of the object which contains "primary": true.
Group mapping
If you would like Group objects in your directory to synchronize with Bitwarden, you may enable or disable Provision Microsoft Entra ID Groups. This option is enabled by default. Select the Provision Microsoft Entra ID Groups link to customize the attributes sent to Bitwarden with the groups objects if you wish to make changes according to the following table:
Bitwarden attribute | Default AAD attribute |
|---|---|
|
|
|
|
|
|
Under the Settings dropdown, choose:
Whether to send an email notification when failure occurs, and if so, what address to send it to (recommended).
Whether to sync only assigned users and groups or sync all users and groups. This setting is modified based your Mapping configuration. For example, if Group mapping is disabled, Groups added to the Enterprise Application will synchronize only the User objects who are members of the Group, and not create the Group in Bitwarden itself. If you choose to sync all users and groups, skip the next step, as your entire directory will be synchronized, depending on your Mapping settings.
Complete this step if you have selected to sync only assigned users and groups from the provisioning settings. Select Users and groups from the navigation:
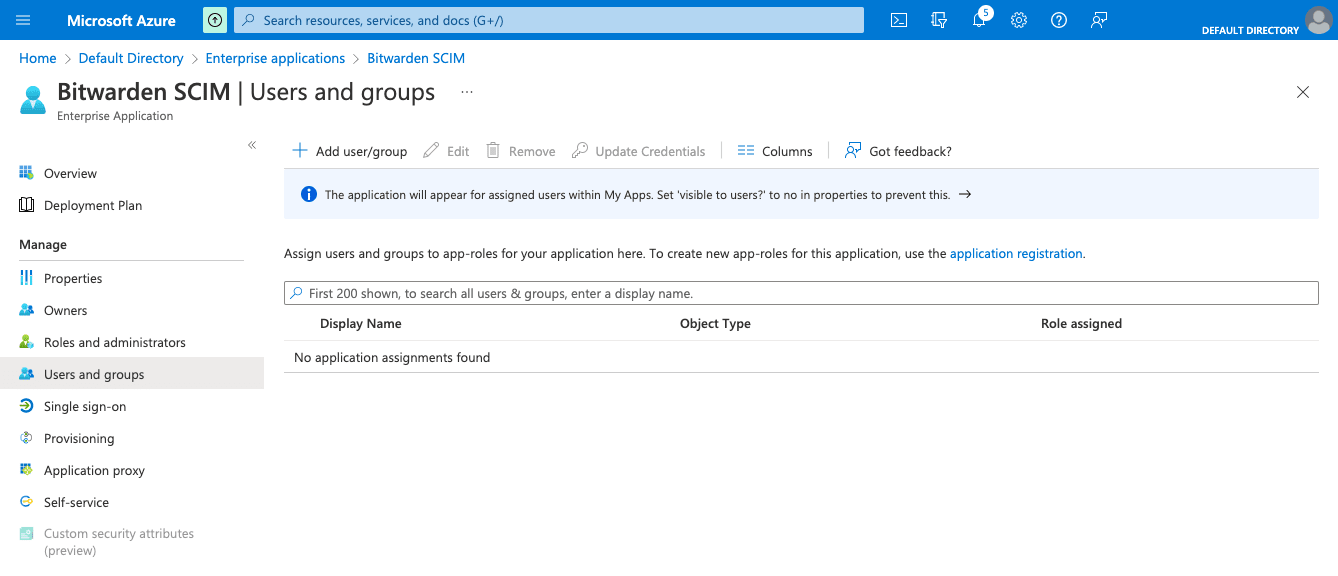
Select the Add user/group button to assign access to the SCIM application on a user or group level. The following sections describe how modifying users and groups in Azure will impact their counterparts in Bitwarden:
Users
If Provision Microsoft Entra ID Users has been enabled in your Mappings, the following actions are taken:
When a new user is assigned in Azure, the user is invited to your Bitwarden organization.
When a user who is already a member of your organization is assigned in Azure, the Bitwarden user is linked to the Azure user through their
UserNamevalue.Users linked in this way are still subject to the other workflows in this list, however values like
displayNameandexternalId/mailNicknameare not automatically changed in Bitwarden.
When an assigned user is disabled via the
accountEnabledproperty in Azure, the user has their access to the organization revoked.When an assigned user is "soft" deleted in Azure, the user has their access to the organization revoked.
When the user is permanently deleted in Azure, the user is removed from the organization.
When an assigned user is removed from the Enterprise application in Azure, the user has their access to the organization revoked.
When an assigned user is removed from a group in Azure, the user is removed from that group in Bitwarden but remains a member of the organization.
Groups
If you have Provision Microsoft Entra ID Groups enabled in your Mappings, the following actions are taken:
When a new group is assigned in Azure, the group is created in Bitwarden.
Group members who are already members of your Bitwarden organization are added to the group.
Group members who are not already members of your Bitwarden organization are invited to join.
When a group that already exists in your Bitwarden organization is assigned in Azure, the Bitwarden group is linked to Azure through the
displayNameandexternalId/objectIdvalues.Groups linked in this way will have their members synced from Azure.
When a group is renamed in Azure, it will be updated in Bitwarden as long as the initial sync has been made.
When a group is renamed in Bitwarden, it will be changed back to what it's named in Azure. Always change group names Azure-side.
Once the application is fully configured, start provisioning by selecting the Start provisioning button on the enterprise application's Provisioning page:
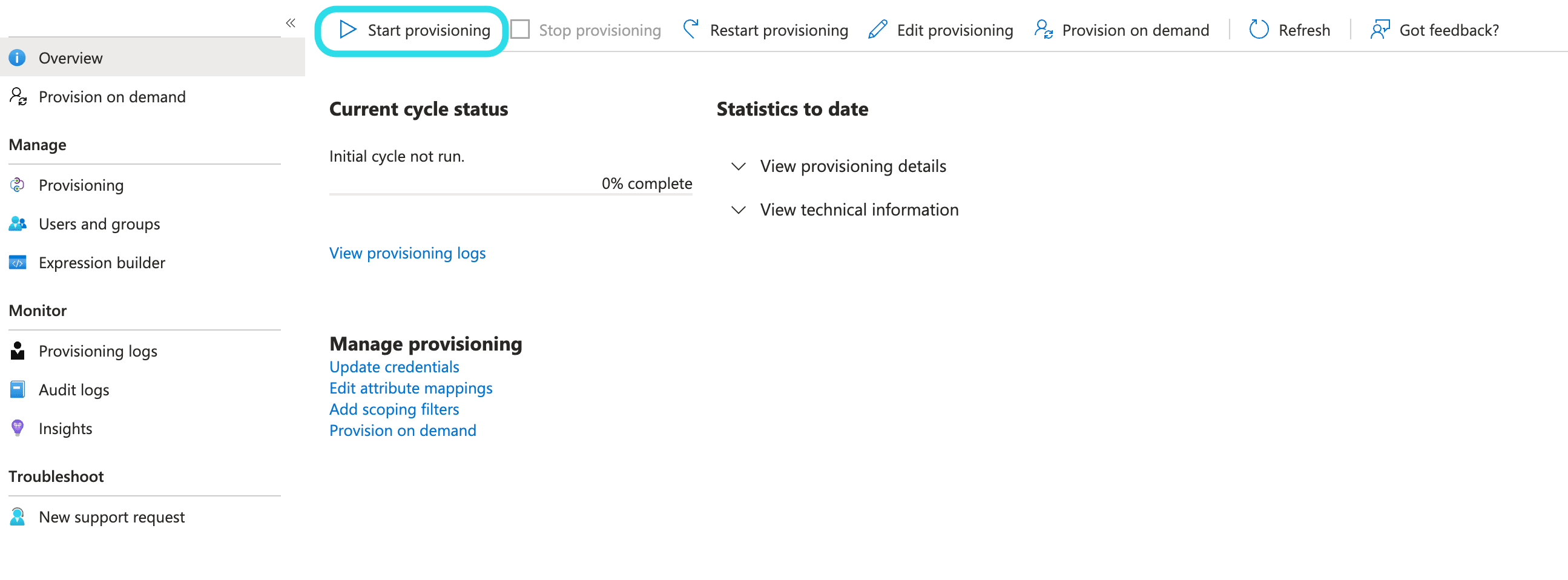
Now that your users have been provisioned, they will receive invitations to join the organization. Instruct your users to accept the invitation and, once they have, confirm them to the organization.
note
The Invite → Accept → Confirm workflow facilitates the decryption key handshake that allows users to securely access organization vault data.
Suggest changes to this page
How can we improve this page for you?
For technical, billing, and product questions, please contact support